| |
It will be a two hour, in-class examination.
You are permitted to bring and use one 3x5 paper study card, which you will submit with your exam.
It may be prepared in any manner you choose.
The exam covers Chapters 1 - 17. It is a comprehensive exam, with at least half the questions coming from material since the second midterm exam.
No electronic devices of any kind are permitted.
Expectations:
- See course goals and objectives
- See objectives at the beginning of each chapter
- See Summary at the end of each chapter
-
See previous exams:
See also Dr. Barnard's notes. He was using a different edition of our text, so chapter and section numbers do not match, but his chapter summaries are excellent.
In the Table of Contents or the Index to the text, can you define/explain each term?
Directions:
Read and follow the directions.
- Write on five of the six questions. Each question is
worth 20 points. If you write more than five questions, only the first
five will be graded. You do not get extra credit for doing extra problems.
- In the event this exam is interrupted (e.g., fire alarm or bomb threat), students will leave their papers on their desks and evacuate as instructed. The exam will not resume. Papers will be graded based on their current state.
- Read the entire exam. If there is anything you do not understand about
a question, please ask at once.
- If you find a question ambiguous, begin your answer by stating clearly
what interpretation of the question you intend to answer.
- Begin your answer to each question at the top of a fresh sheet of
paper. [Or -5]
- Be sure I can read what you write.
- Write only on one side of a sheet.
- Be sure your name is on each sheet of paper you hand in. [Or -5]
Question: Could you send an email about what we REALLY should focus on as we prepare for the exam?
I ABSOLUTELY get it that the exam appears to you very differently from how it appears to me. You have 28 different exams to look at as examples of questions I might ask, so you are able to judge from what I DO, as well as from what I say. This year, since I am allowing you to bring a study card, there might be fewer questions taken directly from previous exams.
See what we claim as Course Goals and Objectives
Some questions are adapted from questions previous students have reported being asked about operating systems at an interview.
Of course, there will be a vocabulary question, in some form. You should AT LEAST know what each line in the Table of Contents means.
Of course, there will be a tricky C question.
I like to ask a question or two in which you apply knowledge you should know to a situation you may not have considered.
If I will ask 6 questions (you write on 5) from 17 chapters, a final examination is a random sampling process. I cannot possibly ask about everything. It may not look like it to you, but I think I try to ask primarily high level conceptual questions, not tricky, detailed questions (except for the tricky C question, which is, well, tricky).
I always am tempted to ask, "What are the five BIG CONCEPT of operating systems? What concept would you rate as #6? Why is it not as important as the first 5?" I will NOT ask that because I do not know how to grade it fairly, but it is a question you should be able to answer.
Score Distribution:
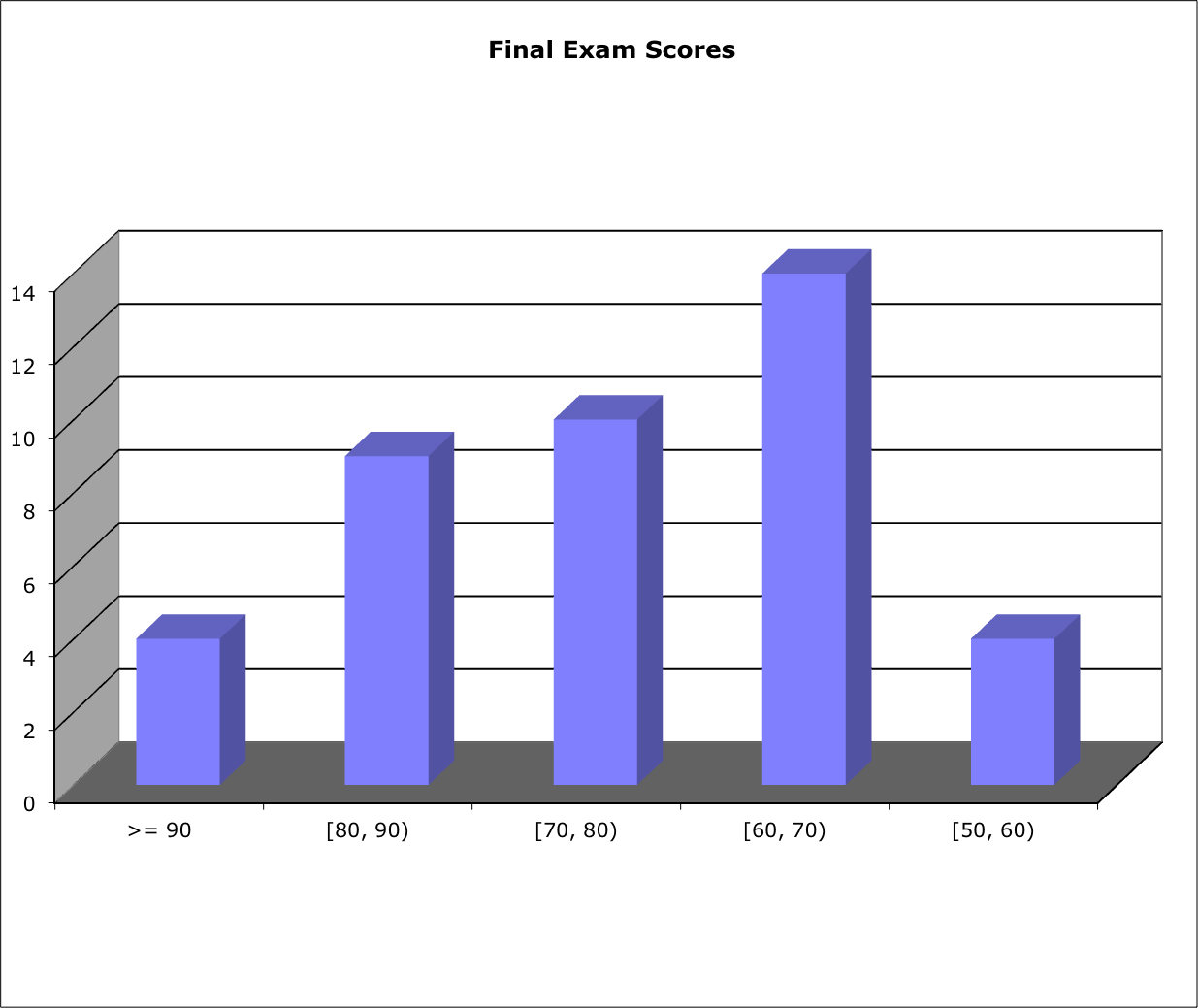
Range: [31, 94]; Median: 70; Mean: 71.0; Standard Deviation: 14.5
These shaded block are intended to suggest solutions; they are not intended to be complete solutions.
Problem 1 Compare and Contrast
Problem 2 Starting Your Computer
Problem 3 Real-Time Operating Systems
Problem 4 Tricky C - FiSH
Problem 5 Disk Scheduling
Problem 6 Network Neutrality
Problem 1 Compare and Contrast
In the context of computer operating systems, compare and contrast each pair of terms:
- Define each term
- How are they similar?
- How are the different?
- Process vs. thread
- Paging vs. segmentation
- Protection vs. security
- File vs. directory
- LAN vs. WAN
- Compare Chapters 3 & 4.
Process: (p. 99) Program in execution, a unit of work in a modern time-sharing
system.
Thread: (p. 153) Basic unit of CPU use. It comprises a thread ID, a program counter, a register set, and a stack.
Similar: Both are units of execution; both are scheduled.
Different: Terminology differs from one operating system to another. In our text, a process may consist of several threads. A thread is a "lightweight process." A process includes a code section of memory, a data section of memory, and other operating system resources such as open files and signals. These resources are shared by sibling threads.
- See Chapter 8, especially Sections 8.4 - 8.6.
Paging: (Section 8.4) Memory management scheme permitting the physical address space of a process to be non-contiguous. A page table maps pages in logical memory to page frames in physical memory.
Segmentation: (Section 8.6) Similar to Paging, except that segments are related portions of code and data.
Similar: Both are memory management schemes permitting the physical address space of a process to be non-contiguous. In both, blocks of logical memory are swapped back and forth between disk and main memory.
Different: Pages are all the same size; segments can be different sizes. Page boundaries are determined by the operating system and the hardware; segment boundaries are determined by the programmer or the compiler. Page boundaries have no relation to the context; segments contain related code or data.
- See Section 1.9 and Chapters 14 & 15.
Protection: (p. 591) Mechanisms for controlling the access for programs, processes, or users to the resources of a computer system. Protection includes measures to prevent ourselves from doing something stupid. Protection is an internal problem.
Security: (p. 621) Guarding against unauthorized access, malicious destruction, and accidental introduction of inconsistency. Security faces externally.
Similar: Both concern ensuring that our computers are available for appropriate use.
Different: Protection is an internal problem, defending against threats originating on the same machine. Security faces externally, defending against threats originating from other machines.
- See Chapter 10.
File: (p. 422) A named collection of related information recorded on secondary storage.
Directory: (p. 433) A named collection of files that records information such as name, location, size, type for all files in that directory.
Similar: Both share many attributes and operations. In many operating systems (e.g., Unix-like), they share a common data structure, an inode.
Different: A directory is a collection of files. Some attributes and operations are different.
- LAN: (p. 31) Local Area Network - Typically, all machines on a LAN communicate with each other directly.
WAN: (p. 31) Wide Area Network - Typically, machines on a WAN communicate through intermediate routers and gateways.
Similar: Both refer to collections of communicating computers
Different: Distance - LANs connect machines that are physically close, while WANs connect machine that are spread across a (relatively) wide geographic area.
Definitions from previous final exams (older page numbers refer to older editions of our text):
2012:
- FCB - File Control Block (p. 463): (an inode in most UNIX systems) contains information about a file.
- RPC - Remote Procedure Call (p. 131): Abstract the procedure-call mechanism for use between systems with network connections.
- SMP - Symmetric Multiprocessing (p. 202): Each processor is self-scheduling.
- TLB - Translation Look-aside Buffer (p. 333): Special, small, fast hardware look-up table often used to store a page or segment table in a virtual memory system.
- INODE - Trick question. Not an acronym. (p. 463) Traditional variable name in UNIX source code for the File Control Block.
- SSTF - Shortest Seek Time First disk scheduling (p. 512): Service all requests close to the disk head before servicing requests far away.
- RAID - Redundant Arrays of Independent/Inexpensive Disks (Section 12.7).
- HTTPS - Hypertext Transfer Protocol (Secure). Protocol for in which web pages and responses requiring secure communications (e.g., login or personal information) are communicated.
- MAC - Medium Access Control (p. 699): Unique byte number assigned to every Ethernet device for addressing on its Ethernet.
- DNS - Domain Name System/Service (p. 448). Provides host-name-to-network-address translations.
2011:
- SMP, p. 14: Symmetric Multi-Processor
- IPC, p. 116 ff.: Interprocess Communication
- RAID: Section 12.7: Redundant Arrays of Independent (or Inexpensive) Disks
- PCB, p. 103: Process Control Block
- RPC, p. 131: Remote Procedure Call
- POSIX: Portable Operating System Interface for Unix
- SJF, p. 189: Shortest Job First CPU scheduling algorithm
- TSR: Terminate and Stay Resident
- TLB, p. 333: Translation Look-aside Buffer
- LRU, p. 376: Least Recently Used
- LAN, p. 31: Local Area Network
- WAN, p. 31: Wide Area Network
- pid: Process Identifier
- FCB: File Control Block
- X - CLI, p. 50: Command Line Interface
- X - MMU, p. 319: Memory-Management Unit
2010:
- PCB - Process Control Block (p. 103): Representation of a process in the operating system.
- IPC - Interprocess Communication (Section 3.4)
- SJF - Shortest Job First scheduling (p. 189): The next process assigned to the CPU is the one with the shortest expected execution time.
- LWP - Lightweight process (p. 199): Sometimes used as a synonym for a thread.
- MUTEX - Mutual Exclusion (Chapter 6): When one process is executing in its critical section, no other process is allowed to execute in its critical section.
- VFS - Virtual File System (p. 468): A layer in the file system interface . It separates file-system-generic operations from their implementations, and it provides a mechanism for uniquely representing a file throughout the network.
- NFS - Network File System (p. 490): Both an implementation and a specification of a software system for accessing remote files across a network.
- SCAN - Trick question. Not an acronym. (p. 513) The disk arm starts at one end of the disk and moves toward the other end, servicing requests as it reaches each cylinder, until it gets to the other end of the disk.
- FTP - File Transfer Protocol (p. 676)
- TCP/IP - Transmission Control Protocol/Internet Protocol (p. 693): Combination of a reliable, connection-oriented Transport Layer and the protocol responsible for routing IP datagrams through the Internet.
2008:
- Operating system (p. 3) A program that manages the computer hardware,
provides a basis for application programs, and acts as an intermediary between
the computer user and the computer hardware.
- Process (p. 81) Program in execution, a unit of work in a modern time-sharing
system.
- Starvation (p. 163) A process is ready to run but kept waiting indefinitely,
usually while other, higher priority processes are served. Not deadlock.
- Interrupt handling (See Section 13.2.2)
- File (p. 374) A named collection of related information recorded on secondary
storage.
- Indexed file access (p. 384) Similar to direct file access, except that
an index is used to record pointers to blocks of a file. To find a record
in the file, we search the index and use the pointer to access the file
directly. Not the same as direct file access.
- Thrashing (p. 343) Large numbers of page faults as pages are repeatedly
brought in and swapped out.
- Communication protocol (Section 16.6) A set of standards specifying syntax
and semantics for peer-to-peer communication across a network.
- Network topology (Section 16.4) Manner in which multiple computers are
connected.
- Security (p. 559) Guarding against unauthorized access, malicious destruction,
and accidental introduction of inconsistency. Security faces externally.
Security is not the same as protection.
- Operating system (p. 3) A program that manages the computer hardware,
provides a basis for application programs, and acts as an intermediary between
the computer user and the computer hardware.
- Thread (p. 127) Basic unit of CPU utilization; a thread ID, a program
counter, a register set, and a stack.
- Deadlock (p. 204) Two or more processes are waiting indefinitely for an
event that can be caused only by one of the waiting processes.
- Atomic instruction (p. 198) Executes as a unit. Either completes without
interruption or has no effect.
- Directory (see p. 386) A named collection of files that records information
such as name, location, size, type for all files in that directory.
- Direct file access (p. 383) A file is viewed as a numbered sequence of
fixed-length blocks or records. Direct access refers to access to records
within the file, not to files as units.
- Working set size (p. 346) Set of pages in the most recent page references.
- RAID (p. 468) Redundant Arrays of Inexpensive (or Independent) Disks
- Remote procedure call (p. 825) A client-server mechanism that enables
an application on one machine to call a procedure on another machine.
- Protection (p. 531) Mechanisms for controlling the access for programs,
processes, or users to the resources of a computer system. Protection is
an internal problem. Protection != security.
2007:
- Thrashing: see section 9.6, p. 343. High paging activity. Process is using
more pages than it holds page frames.
- Wait() operation? See section 6.5, p. 200. Indivisible operations which
behaves like
wait(semaphore S)
{
while (S <= 0) ; // Typically sent to a waiting queue
S--;
}
- Direct file access: see section 10.2.2, p. 383. File is viewed as a numbered
sequence of blocks or records
- What is the "Readers-Writers Problem?" See section 6.6.2, p.
206. Multiple instances of one type of process seeks to read from a shared
memory location, file, or database. Multiple instances of a second type of
process seeks to write to the same shared location.
- Working set: see section 9.6, p. 345: The set of pages in the most recently
referenced Delta page references.
- Semaphore signal() operation? See section
6.5, p. 200: An indivisible operation with the effect of
signal(semaphore S) { S++; }
and releases a waiting process, if any.
- Indexed file access: see section 10.2, p. 384 ff.: Records in a file
are accessed directly using a key or index
- "Dining Philosopher's Problem?" See section 6.6, p. 207 ff.:
Five philosophers spend their lives thinking and eating. Draw a picture
similar to Figure 6.14.
Our field is full of TLA's (Three Letter Abbreviations) that are convenient short-hand for insiders, but barriers to understanding by outsiders. We had a bad reputation in many quarters for over-use of jargon, sometimes with the intent to confuse. Don't be like that. Speak English with your stakeholders.
Problem 2 Starting Your Computer
What happens when you turn your laptop/desktop computer on, up to the point it is ready for you to begin using it? Give a step-by-step sequence. Be as specific as you can.
Step 0: Press the [Power ON] switch
[Your answer fits here]
Step N: You can click the mouse, swipe your finger across the screen, or type commands, and your computer responds.
Between Steps 0 and N, I expect you to identify 5 - 10 steps, depending on what you count as a "step."
For each step, discuss
- What is the role or purpose of this step?
- How and where is the software found that executes in this step?
- What does the software accomplish in this step?
By the time you get to Step N, your computer has several tens of processes running, it is managing its memory, it knows about the attached disk drives and file systems, and it is communicating on a network. Your answer needs to explain how and when each of those services gets started and initialized.
Descriptions are scattered throughout the
text. Can you integrate them? In brief:
- Must start executing code from nonvolatile Read Only Memory [or -4]
- which checks hardware and
- reads a loader from fixed location on disk or network
- which loads the full OS from disk or network
- initializes system tables
- starts various OS processes using FORK
- including command processor and/or GUI event handler [or -2]
- start user processes
This level of detail earns C. More detail is expected for scores > 10.
It is critical to tell where to find each loader and the OS itself.
Since the problem specifically mentioned "ready for
you to begin using it," you lost 2 points if you did not explicitly mention
something about receiving user input.
If you describe what you see on the screen (external manifestations) vs. the
inner workings, you earn 8 of 20 points.
Problem 3 Real-Time Operating Systems
Background: For the purposes of this question, let us use the term "PC" to refer to the conventional laptop and desktop personal computer we use routinely, without regard to the operating system. For this discussion, an Apple Mac is considered a "PC."
For the purposes of this question, let us use "embedded systems" and "real-time systems" to mean the same thing.
Our text uses the term "real-time embedded systems."
Some may object to these definitions, but I want you to discuss broad classes of computer systems and not worry about fine distinctions, no matter how commercially significant those distinctions might be.
Questions:
- How would you define a real-time embedded system?
- Give three examples. You do not have to describe them; I just want to understand what you intend in part a)
- An operating system manages CPU time through managing processes. How must an operating system for real-time embedded systems differ from a PC operating system in its management of processes?
- An operating system manages memory. How must an operating system for real-time embedded systems differ from a PC operating system in its management of memory?
- An operating system manages external storage, including disks and file structures. How must an operating system for real-time embedded systems differ from a PC operating system in its management of external storage?
- An operating system manages input and output. How must an operating system for real-time embedded systems differ from a PC operating system in its management of input and output?
- An operating system manages network communications. How must an operating system for real-time embedded systems differ from a PC operating system in its management of network communications?
Enumeration of the role of an operating system as a resource manager in parts c) - g) should have been part of the question, but I listed them for you so we are all addressing the same questions.
For simplicity here, I use the acronym "RTOS" for "Real-Time (Embedded) Operating System."
- (4 points) A real-time embedded system is a device (or a collection of devices) whose design includes one or more computers, but the computer is not the main purpose of the device. A real-time system typically has well-defined, fixed time constraints. Its computer(s) typically communicate with the rest of the device through sensors and activators of varying sorts. Its computers usually have no "user," in the PC sense. Key differences include deadlines, need for predictability, and limited resources.
- (4 points) Examples include
- Medical devices from simple, one-variable patient monitors to complex imaging systems;
- Cars, airplanes, ships, CAT/JOY shovels, etc.;
- Machine tools, factory processes, and robots;
- Appliances: radios, TVs, microwaves, washers (AO Smith sells a hot water heater with an IP address);
- Assistive technology devices;
- Cell phones? I'll accept that, but I think the power and versatility of our phones is approaching that of our computers. A smart phone is far more than a device for making telephone calls. It has become a general-purpose computer in its own right.
Your answers to the following can vary considerably, depending on the scale of embedded devices you consider. The RTOS for a CT scanner is very different from that for a blood pressure monitor, or a mining shovel compared with a microwave.
- (4 points) Managing processes: RTOS must be predictable. CPU use often is managed entirely by interrup-handling. Often, an RTOS must guarantee a level of service and/or deadline scheduling. It cannot tolerate the seemingly stochastic properties of PC precess-scheduling methods. A smaller RTOS does not support both processes and threads. A small RTOS may support only a single application process, in which case, it may do no scheduling (as we discussed it) at all. A large RTOS for a complex application has all the features of a PC scheduler, PLUS guaranteed service and deadline guarantee scheduling.
- (2 points) Managing memory: RTOS must be predictable. In smaller applications, applications may be entirely memory resident, so memory management looks like Figure 8.1, p. 316. Garbage collection (and hence any dynamic memory management) often is not supported to avoid unpredictable delays. A large RTOS for a complex application has all the features of a PC memory manager, PLUS guaranteed-time memory allocation and de-allocation.
- (2 points) Managing external storage: Most real-time systems have none, but large RTOS for a complex application has all the features of a PC external storage manager, PLUS techniques for managing the delay and the variability inherent in communicating with external storage units. Alternatively, external storage may be accessed over a network, instead of locally.
- (2 points) Managing input and output (I/O): Most real-time systems have no display, keyboard, or user, in the usual sense. Their input and output happens via ports, busses, or networks. Any display is for the system, not for the computer(s). Hence, OS support for I/O may be limited to memory-mapped ports and support for interrupt-driven I/O. A large RTOS for a complex application has all the features of a PC I/O manager, PLUS techniques for managing the delay and the variability inherent in I/O.
- (2 points) Managing network communications: Many real-time systems have no network connectivity. On the other hand, full network support is becoming common. AO Smith sells a hot water heater with an IP address and full TCP/IP support.
You earned 15 of the 20 points if you considered only relatively small, limited embedded systems (or if you considered only large, complex embedded systems). To be considered for the full 20 points, you had to at least mention both small and large embedded systems.
Problem 4 Tricky C - FiSH
Here is a tricky C function that might appear in the context of Embedded Xinu's
FiSH protocol daemon:
1:
2:
3:
4:
5:
6:
7:
8:
9:
10:
11:
12:
13:
14:
15:
16:
17:
18:
19:
20:
21:
22:
23:
24:
25:
26:
27: | |
struct fishnode { char used; uchar mac[ETH_ADDR_LEN]; char name[FISH_MAXNAME]; };
struct fishnode school[SCHOOLMAX];
/* Process a FiSH protocol ANNOUNCE packet when it arrives at server. */
/* ANNOUNCE packets are unicast, and contain a null-terminated node name,
followed by zeros padding up to ETHER_MINPAYLOAD size. A
FISH_ANNOUNCE packet is sent by each listening node that receives a
FISH_PING packet. The destination is the FISH_PING source node. */
int fishAnnounce(struct ethergram *eg)
{
for (i = 1; i < SCHOOLMAX; i++)
{
/* Check to see if node already known. */
if (memcmp(school[i]->mac, eg->src, ETH_ADDR_LEN))
return OK;
}
for (i = 1; i < FISH_MAXNAME; i++)
{
/* Else find an unused slot and store it. */
if (school[i].used) {
school[i]->used = 1;
strcpy(school[i]->mac, eg->dst);
strcpy(school[i]->name, eg->data + 1);
}
}
return SYSERR;
} |
What is wrong with this code?
Hint: The errors are many and varied. Identify as many as you can.
- Local variable i is not declared.
- For loop bounds should start with 0.
- Second for-loop should run to SCHOOLMAX, not FISH_MAXNAME.
- Should check school[i].used field first before comparing MAC.
- memcmp returns 0 (false) if the MACs are equal.
- Unused slot should have used == 0, so if condition is wrong.
- Fields of school array must be accessed with '.' instead of '->'.
- Both of the strcpy() calls should be replaced with strncpy() or memcpy(),
which include bounds.
- If-statement inside second for-loop should return OK, otherwise loop
fills in multiple times.
- Ethergram src field needs to be copied into table, not destination.
Problem 5 Disk Scheduling
Suppose we have a disk drive with the following characteristics:
| Platters: |
1 |
|
Rotational speed: |
100 rev./sec. |
| Tracks: |
3000 |
|
Seek speed: |
5 x 104 tracks/sec. |
| Sectors: |
1000 |
|
Data transfer rate: |
108 bits/sec. |
| Bytes per block: |
4048 |
|
|
|
Assume that at time t = 0, the disk controller has received the following
requests in the order shown.
| Request # |
|
Track # |
|
Sector # |
|
Read/Write |
| 1: |
|
2222 |
|
1 |
|
Read |
| 2: |
|
45 |
|
2 |
|
Read |
| 3: |
|
2863 |
|
3 |
|
Write |
| 4: |
|
1234 |
|
4 |
|
Write |
| 5: |
|
1234 |
|
3 |
|
Read |
| 6: |
|
1234 |
|
1 |
|
Read |
| 7: |
|
510 |
|
432 |
|
Write |
Assume no additional requests are received while these requests are served.
Assume the disk head starts at track 2000, sector 0.
At
what time, in seconds, does the disk complete service of these seven requests if the disk controller schedules these requests by
- FCFS
- SSTF
- SCAN
You will need to make additional assumptions. State your assumptions explicitly.
See Section 12.4
Let's simplify this by introducing some variables. Let
| x |
= |
time to read one sector
= 10-5 sec. |
| y |
= |
time to seek one track
= 2 x 10-5 sec. |
Hence, we count in units of 10-5 sec.
and convert to seconds when we are done.
We assume
- While we seek, the disk is rotating, so we must determine at which track
the head is when seek gets to the correct track.
- SCAN goes to track 2999 and starts scanning from there
Spreadsheet I used
- FCFS:
0.204 sec. Service order: 1, 2, 3, 4, 5, 6, 7.
| Request # |
|
Track # |
|
Sector # |
|
Seek time |
|
Latency |
|
Complete |
|
| 1: |
|
2222 |
|
1 |
|
444 |
|
557 |
|
1002 |
| 2: |
|
45 |
|
2 |
|
5356 |
|
646 |
|
6003 |
| 3: |
|
2863 |
|
3 |
|
5636 |
|
364 |
|
12004 |
| 4: |
|
1234 |
|
4 |
|
3258 |
|
742 |
|
16005 |
| 5: |
|
1234 |
|
3 |
|
0 |
|
998 |
|
17004 |
| 6: |
|
1234 |
|
1 |
|
0 |
|
997 |
|
18002 |
| 7: |
|
510 |
|
432 |
|
1148 |
|
982 |
|
20433 |
- SSTF:
0.130 sec. Service order: 1, 3, 4, 5, 6, 7, 2.
| Request # |
|
Track # |
|
Sector # |
|
Seek time |
|
Latency |
|
Complete |
|
| 1: |
|
2222 |
|
1 |
|
444 |
|
557 |
|
1002 |
| 3: |
|
2863 |
|
3 |
|
1282 |
|
719 |
|
3003 |
| 4: |
|
1234 |
|
4 |
|
3258 |
|
743 |
|
7004 |
| 5: |
|
1234 |
|
3 |
|
0 |
|
999 |
|
8003 |
| 6: |
|
1234 |
|
1 |
|
0 |
|
998 |
|
9001 |
| 7: |
|
510 |
|
432 |
|
1448 |
|
983 |
|
11432 |
| 2: |
|
45 |
|
2 |
|
930 |
|
640 |
|
13002 |
Assume: Shortest Seek Time First does not also optimize latency, so
requests in the same track are served FCFS
- SCAN:
0.130 sec. Service order: end, 3, 1, 4, 5, 6, 7, 2. Also acceptable: 1, 3, 2999, 0, 2, 7, (4, 5, 6), and a couple of others.
| Request # |
|
Track # |
|
Sector # |
|
Seek time |
|
Latency |
|
Complete |
|
| |
|
2999 |
|
998 |
|
1998 |
|
0 |
|
1002 |
| 3: |
|
2863 |
|
3 |
|
272 |
|
733 |
|
3003 |
| 1: |
|
2222 |
|
1 |
|
1282 |
|
716 |
|
5001 |
| 4: |
|
1234 |
|
4 |
|
1976 |
|
27 |
|
7004 |
| 5: |
|
1234 |
|
3 |
|
0 |
|
999 |
|
9003 |
| 6: |
|
1234 |
|
1 |
|
0 |
|
998 |
|
9001 |
| 7: |
|
510 |
|
432 |
|
1448 |
|
983 |
|
11432 |
| 2: |
|
45 |
|
2 |
|
930 |
|
640 |
|
13002 |
SCAN starts at one end of the disk. We assume it starts at track 2000, goes
to track 2999, and starts scanning from there.
As our book explains it, LOOK would go from 2000 to 2863, without first going
to the end.
As long as the transfer rate is comfortably larger than the rate at which bits fly under the head,
transfer rate has no effect on your answer.
As stated, Read/Write does not affect on your answer.
It is coincidental that SSTF and SCAN are the same in this example.
The details of these computations are subject to MANY variations. I do not
expect your answers to agree with mine.
You should arrange the requests in the correct order.
SSTF and SCAN should beat FCFS
Time should have correct order of magnitude.
Problem 6 Network Neutrality
Background: "Network neutrality" has become a controversial issue. When your path to the Internet is lightly loaded, it does not matter. However, when network traffic is heavy, gateways and servers along the way may not be able to keep up with the packet traffic. By design, they drop some packets so they can transmit the rest.
The network neutrality question is, "Should Internet Service Providers (ISPs) such as Time-Warner (Roadrunner) be permitted to give preferential treatment to information packets from its own content services and to give poorer service to information packets from its competitors? Alternatively, should customers of an ISP be permitted to pay extra for a premium service, meaning that packets to/from them receive preferential treatment?"
- Some hold that the Internet is a public infrastructure like a highway, and all information packets should be treated equally.
- Others hold that portions of the Internet are commercial enterprises, and providing preferential service to some packets of information represents good customer service and should be permitted.
In the United States, regulation of this question falls to the Federal Communication Commission (FCC).
Suppose you have been called as an expert (on Internet protocols) witness by the FCC.
Question:
If your last name has an ODD number of characters, explain to the FCC how the technology of Internet protocols works (or could work) to provide equal service to all content and to all customers.
If your last name has an EVEN number of characters, explain to the FCC how the technology of Internet protocols works (or could work) to provide a selective advantage to preferred content or preferred customers.
Hint: You are called as a technical witness. Neither the FCC nor I care a whit about your personal opinion or about philosophical BS. Give a technical answer based on your understanding of standard protocols used by today's Internet. As an exam question, your answer should demonstrate that you understand how routing, DNS, the TCP/IP stack, and other Internet protocols work in this context.
The point of dispute is the behavior of the ISPs when their systems are heavily loaded. In that condition, packets are dropped. Of course, we all prefer that all packets are delivered in a timely manner, but that is not what happens.
Reminder: I asked for technical analysis based on your understanding of Internet protocols. Philosophical statements counted negatively.
In the main, "network neutrality" concerns routing, which is the domain of the Internet layer of the TCP/IP stack, and it is the IP protocol that is in action. Packets only are passed to the Host-to-Host Layer (e.g., TCP or UDP) when they have arrived at their destination.
ODD - FOR net neutrality: The standard IP protocol that is responsible for most packet routing on the Internet is obligated to handle packets in FIFO queues or to drop them (possibly with a return message) if it is not able to do so. IP packets carry no priority, hence the standard requires that all packets receive the same treatment. When it is necessary to drop packets, victim packets should be selected at random. Also, any checking necessary to provide preferred treatment represents additional overhead and slows everything a little.
EVEN - FOR advantaged treatment: The standard IP protocol that is responsible for most packet routing on the Internet is obligated to handle packets in FIFO queues or to drop them (possibly with a return message) if it is not able to do so. IP packets carry no priority, but they must carry source and destination information. In the few regrettable instances when we are forced to drop a few packets, we may select victim packets based in part on source or destination information so that customers who have chosen to pay extra for premium levels of service receive such service. Of course, we do our best to provide quality service to all our customers.
Of course, you can selectively drop packets of non-priviledges customers, but I was impressed by the number and variety of means various students proposed to give a performance advantage. Suggestions included use different DNS servers for priviledged customers/content; in DNS caching, selectively choose victim records; route non-priviledged packets intentionally to busy servers (negative load balancing).
Several suggested forcing non-priviledged customers to use the less reliable UDP, while priviledged customers use TCP? That is impractical because it woudl require self-incrimination on client machines in higher layers of the TCP/IP stack. Besides, when it works, UDP is faster, and the ISP might end up providing faster service to non-priviledged customers.
Thank you
We (Drs. Brylow and Corliss) have enjoyed this semester, and not for the stress we may have cause you. We find operating systems exciting and useful, objects of beauty (in a strange way). We hope we have communicated some of our knowledge and excitement.
If you are graduating, congratulations! Look for us at graduation, and we hope you will keep in touch, wherever life takes you.
If you are not graduating yet, we hope to see you next year, perhaps in other classes or just in the halls of Cudahy and Haggerty.
| |

