| |
Instructions before the exam:
Your final examination will appear here.
It will be a two hour, closed book exam.
It is a comprehensive exam, with at least half the questions coming from
Chapters 14 through 16
Expectations:
- See course goals and objectives
- See objectives at the beginning of each chapter
- See Summary at the end of each chapter
- See previous exams: midterm 2000, final
A 2000, final B 2000
- Problems you might consider include: 14.4, 14.5, 14.6, 14.9, 14.11; 15.1,
15.2, 15.3, 15.6, 15.9, 15.11, 15.14, 16.1, 16.3, 16.7, 16.10, 16.15.
; 17.4, 17.5, 17.7, 17.10; 18.1, 18.3, 18.5, 18.7.
If it matters, I will be grading the exam, not the TA. I expect proper English.
See also Dr. Barnard's notes.
He was using a different edition of our text, so chapter and section numbers
do not match, but his chapter summaries are excellent.
Directions:
Read and follow the directions.
- Write on eight of the ten questions. If you write more
than 8 questions, only the first 8 will be graded. You do not get extra credit
for doing extra problems.
- Read the entire exam. If there is anything you do not understand about
a question, please ask at once.
- If you find a question ambiguous, begin your answer by stating clearly
what interpretation of the question you intend to answer.
- Begin your answer to each question at the top of a fresh sheet of
paper. [Or -5]
- Write only on one side of a sheet.
- Be sure your name is on each sheet of paper you hand in.
[Or -5]
Question:
Are you trained somewhere that to write in paragraphs? Yes, that is often
the preferred means, but in many technical circumstances, including this exam,
outlines, enumerations, bullets, and pictures may communicate more effectively.
At the very least, you should answer by question parts:
-
-
-
For my convenience of scoring, I made each problem worth 20 points. Hence, a perfect exam
is worth 160 points. Your raw score is converted into a percentage.
Grades:
Average score: 76%
Range: [41, 96]
Distribution:
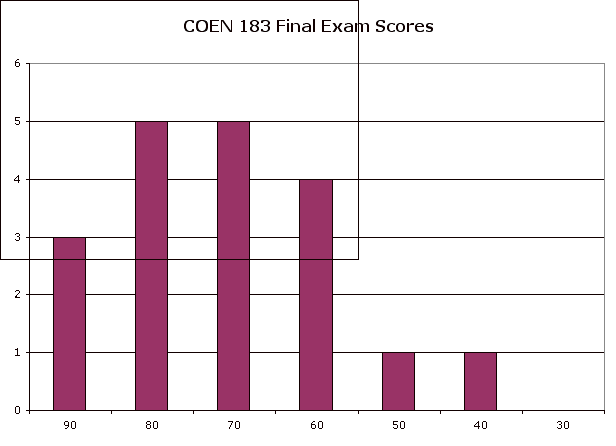
nbsp;
Problem 1. Caching
13 of 19 students selected. Average score: 15 of 20
- What is caching, in the context of computer operating
systems?
- List four different contexts in which caching is a possible solution
- What are the advantages of caching?
- What are the disadvantages of caching?
- Keeping a local copy of remote information.
- Memory <--> disk, OS disk directories <--> on-disk disk directories, disk
files, local disk files <--> remote disk files, domain name service, TLB
<--> in-memory page table, browser or gateway can cache web pages
- Speed, reduced bus/network traffic. Advantages means
more than one.
- Consistency, coherency, cost, complexity of hardware and OS, small size,
slower on a miss than direct access. Disadvantages means
more than one.
See chapters on memory, files, distributed systems. Chapter 1 has a summary. See problems 1.13 & 1.14.
-4 if all your examples are memory caching of disk, which I would consider one context.
Caching as an aspect of virtual memory or networking, but it is not the same.
Caching does not provide a larger address space, for example, although it enables
virtual memory to do so.
Problem 2. User vs. kernel mode
11 of 19 students selected. Average score: 12 of 20
- What is user mode execution?
- What is kernel mode execution?
- In your syncdir assignment, you use operating system calls to retrieve contents of directories, retrieve statistics
of files, open and close files, read and write files. Which are probably executed in user mode? Which are probably
executed in kernel mode? Why?
See Section 1.5.1. The distinction is at the level of individual instructions, or blocks of instructions,
not at the process or thread level. It is not the case that kernel processes
run in kernel mode and user processes run in user mode. What
users write is executed in user mode, but much of the code in many
system calls is executed in user mode, too. Kernel mode is one means
of enforcing certain types of mutual exclusion.
Alternative view: All system calls are executed in kernel mode.
Compromise: Most system calls that are made from user programs are high-level
system calls which execute in user mode, except when they make low-level
system calls to manipulate OS data structures or resources. The low level
calls execute in kernel mode.
- Normal or default level of privilege. The operating system enforces restrictions
on operations and references. Rule of thumb: If the data structure being
manipulated is stored in the address space
of
a
single
process,
its
manipulation is done
in user mode.
- Allows execution of privileged instructions which might interfere with
other users. User processes are switched to kernel mode for critical operations,
especially the manipulation of OS tables. Rule of thumb: If the data structure
being manipulated is stored in the address space of the OS (or is shared
by several processes), its manipulation is done
in kernel mode.
- Trick question. Most of the OS calls in your syncdir assignment execute partially in user mode
and partially in kernel mode.
Problem 3. Boot
11 of 19 students selected. Average score: 15 of 20
What happens when you turn your computer on, up to the point it is ready for
you to begin using it? Give a step-by-step sequence. Be as specific as you
can.
See pp. 71-72, 414, 463-464, 573, 810-811.
I asked this question because descriptions are scattered throughout the
text, and I want to see if you can integrate them.
In brief:
- Must start executing code from nonvolatile Read Only Memory [or -4]
- which reads a loader from fixed location on disk or network
- which loads the full OS from disk or network
- initializes system tables
- starts various OS processes
- including command processor and/or GUI event handler [or -2]
This level of detail earns C. More detail is expected for scores > 10.
It is critical to tell where to find each loader and the OS itself.
Since the problem specifically mentioned "ready for
you to begin using it," you lost 2 points if you did not explicitly mention
something about receiving user input.
If you describe what you see on the screen (external manifestations) vs. the
inner workings, you earn 8 of 20 points.
Problem 4. Threads
15 of 19 students selected. Average score: 15 of 20
Discuss the notion of a thread.
Your answer is at most one page, one side. Answer as you might in a job interview.
Chapter 4. If you wish to convince a job interviewer you understand threads,
you might address:
- Role: Threads provide one means for a computer operating system to manage
the resource of CPU time. One process may consist of multiple threads.
- Threads are similar to processes. Tell how. E.g., scheduling.
- Threads are different from processes. Tell how. E.g., memory. Processes
are copies; threads share. If you say a thread is smaller or lighter weight,
you should tell what is missing.
- Give an example in which treads might be used. Tell why.
-4 if you do not explain how a thread is different from a process.
-2 if you do not tell what threads are good for or give an example application.
I expect some detail to demonstrate more than superficial understanding.
I allowed a page. You should use most of it.
Problem 5. Need to know
17 of 19 students selected. Average score: 17 of 20
- What is the need to know principle?
- Why is it important for a protection system to adhere to this principle?
Problem 14.9, p. 557.
See p. 532. Also known as the principle of least privilege.
An entity (user, process, object, etc) is provided access to only the information it needs to complete its task, only for the time it is necessary, and only
in the modes it requires. For example, if a function needs to read the value
of
a variable,
but may
not
also change
that variable.
Violations of need to know can lead to inappropriate, intentional or unintentional
reading or altering of data. They also make system maintenance more difficult.
An example is helpful.
Few operating systems (or applications) adhere to the need to know principle.
Problem 6. Encryption
17 of 19 students selected. Average score: 13 of 20
- What is the authentication problem?
- What is the secrecy problem?
- Discuss how asymmetric encryption can be used to achieve authentication
Problem 15.14, p. 605.
See Sect. 15.4.1.3.
- (5 points) Who are you? Can you prove it? Authentication does not concern
a person in the middle.
- (5 points) The author can ensure only intended readers can read. "Keeping
sensitive information secret" is a circular definition and earns zero points.
Secrecy
is not just
for communication; I might encrypt information that no one but me should
know.
- (10 points) Asymmetric encryption includes public/private key encryption.
Assume I am sending something, and you want to be sure it really comes from
me.
- I am the only one who holds my private key.
- Anyone may know my public key.
- I encrypt using my private key, which only I know.
- You decrypt using my public key.
- If that works, the message must have come from me, because I am the only
one who could have encrypted it using my private key
For normal encryption, I encrypt with your public key, and you decrypt with
your private key.
(-6 if you claim that is authentication)
Exchanging certificates or relying on a certification authority are methods for
dealing with authentication, but do not use asymmetric encryption.
Problem 7. Distributed systems
17 of 19 students selected. Average score: 12 of 20
Why do we build distributed computer systems?
See p. 612:
- Resource sharing
- Computational speedup
- Reliability
- Communication
Problem 8. Network topology
18 of 19 students selected. Average score: 17 of 20
- Describe or draw a picture to illustrate
- Fully connected network
- Star network
- Ring network
- If a network has 12 members, how many connections are required for a
- Fully connected network
- Star network
- Ring network
- If a network has N members, how many connections are required for a
- Fully connected network
- Star network
- Ring network
See Figure 16.4, p. 621
- Fully connected network: 1 + 2 + ... + (N-1) = N (N-1) / 2 = O(N2)
- Star network: N-1
- Ring network: N
Problem 9. Distributed file protection
14 of 19 students selected. Average score: 15 of 20
In a network or a distributed file system, suppose
- File read.me is owned by user corlissg
- File read.me is readable by world
- Your process opens the file read.me and begins to read
- Before your read is complete, I change the file read.me protections so
the file is no longer readable by you.
- List three alternative operating system responses
- List advantages of each of your alternative responses
- List disadvantages of each of your alternative responses
- What is your preferred alternative? Why?
See p. 546.
The operating system might:
- Do nothing. Permission is only check when you start.
+ Simple
- Not responsive to permission changes
- Deny you access. Permission is checked on each access.
+ Enforces current permissions
- Expensive to maintain coherency and consistency
- Expensive to check every access
- Deny you access later. Delays in propagating permissions cause consistency errors.
+ Compromise
- Compromise
- Force you to wait to see whether I restore your permissions later.
+ Good for temporary interruptions in permission
- Waste for permanent changes in permission
- Allow you to read any portions you have already fetched and buffered, but
not allow new accesses to my copy.
+ Relatively simple, low overhead
- Delays responding to changes in permission
- Reacquisition. Periodically, your process must reacquire the read capability
+ Inexpensive means of propagating changes to access rights
- Delays responding to changes in permission
- Don't let me change access rights while you are reading (Windows' approach)
+ Open access for you to read
- Open access in spite of my desire to protect
- I suppose CRASH is always an alternative, but if the operating system
discovers the difference enough to cause a crash, it might as well respond
in a more reasonable manner.
Which? Depends on the application. (-4 if you give only one answer)
If there are temporary changes in permissions, #4 is good. E.g., Deny read
access during an update operation.
If security is more important than performance, #2 is good.
If security is less important than performance, #1 or #5 is good.
Problem 10. Process improvement:
19 of 19 students selected. Average score: 19 of 20
We encourage you to continuously improve your processes. We also should
continuously improve ours.
- List topics covered in this class that duplicated coverage in other classes
you have taken. Which other classes?
- Suggest one topic to be added to this class. Why?
- Suggest one topic to be omitted from this class. Why?
- Duplicated coverage:
- Paging, caching, page faults, virtual memory, TLB: COEN 171
- C coding
- Network topology: COEN 020 or 030, BIEN 112
- Boot sequence: COEN 171
- Software testing: COEN 191
- Much of COEN 020, but not in as much depth
- Cryptography: Intro to Algorithms
- Process scheduling, process control block, context switching: BIEN 112
- Security and protection: BIEN 121
-
- Add:
- History, workings, and differences of commercial operating systems
- Wireless networking
- Tutorial on C programming and suggest a book
- File compression
- CISCO
- Last chapter of the book
- More on Internet communication across a network
- Embedded and real-time OS
- Explain sockets, if you expect us to use them for homework
- Another practical application like GNU Privacy Guard
- RAID
- Data streams
- Study an actual operating system to see how it all comes together
- How hacks are done
- More on networking
- Shell scripting and Unix commands
-
- Omit:
- Much of the memory management: Overlaps COEN 171
- Networking: leave more time for OS
- Protection/access matrix
- Do NOT omit networking
- Nothing (-2)
- Much of file management or file system implementation. Perhaps focus on
Chapter 11 and go lightly on Chapter 10.
- Details on CPU scheduling, page replacement, etc. I can learn them on my
own. Other material needed help.
- SSL & HTTP are networking applications, not OS
- Less process stuff, perhaps deadlocking
-
- I'm surprised no one listed assessment surveys, including this question :-)
I appreciate your responses. It appears that we might leave most of the memory
management part to COEN 171, leaving this class time to do more justice to networking,
since this
is supposed to be a networking class.
| |

